Burp Suite Intruder Attack Types
Simple list Runtime file Custom iterator Character substitution Case modification Recursive grep Illegal Unicode Character. Burp intruder has four attack types which are sniper.
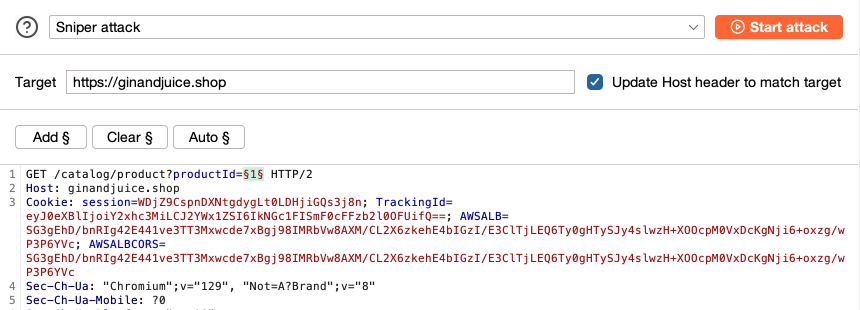
Using Burp Intruder Portswigger
Activate the Burp Proxy and attempt to log in.
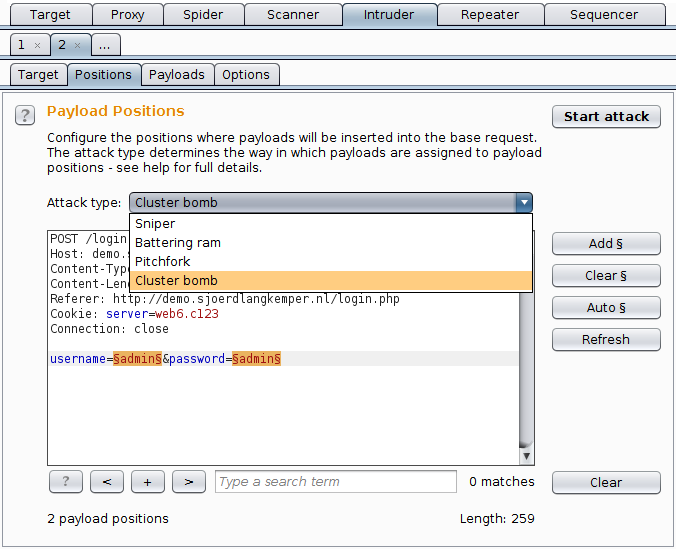
. About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy Safety How YouTube works Test new features Press Copyright Contact us Creators. This attack type is useful when brute-forcing credential if you have a list of candidate usernames and a list of candidate passwords but you dont know which corresponds to which. This is Burp Suite for Web Application Security - 10 - Intruder Attack Types by Bucky Roberts on Vimeo the home for high quality videos and the people.
Configure the positions the same way as we did for bruteforcing the support login. Burp Intruder includes the following payload types. The attack type can be selected using the drop.
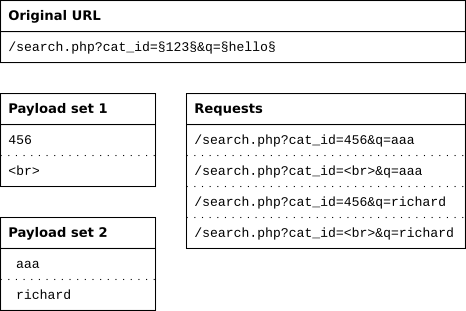
After all values are exhausted the second position is used and the first position is left. The Video Content has been made available for informational and educational purposes only. Attack Types Sniper If you were using Sniper to fuzz three parameters in a request with a wordlist containing 100 words how many requests would Burp Suite need to send to.
Burp intruder tool can be used as a fuzzer and a tool for performing brute force attacks and many other purposes. Jovialism does not make any representation or warranties with resp. First the first position is replaced by values from the payload set and the second position is left alone.
Videos based upon the profounded Youtube Techie- Bucky Roberts. All about Intruder Attack Types. Burp Suite Tutorial - Intruder Attack with Simple list Payload setBurp Suite is a tool or set of tools used for penetration testing of web applications It is one of the most popular tools.
Throughout this room well take a. Capture the request and send it to Intruder. It can be used to automate all kinds of tasks that may arise during your testing.
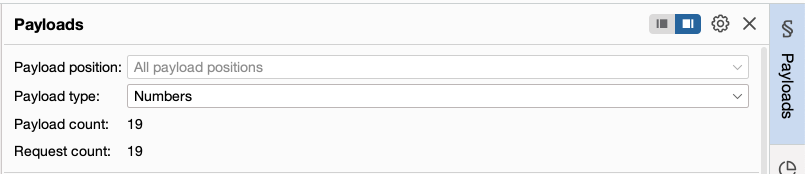
Burp Intruder supports various attack types - these determine the way in which payloads are assigned to payload positions. Hereby I am uploading the 10 tutorial on Burp Suite. Burp 20215 released for early adoptersSay hello to some massive updates to IntruderYou can now save the Intruder attack payloads and their corresponding responses to Burp project files.
Burp Intruder is a powerful tool for automating customized attacks against web applications. Do subscribe the channel to get to. The easiest way to set up the Target field and request template is to select the request you want to attack anywhere within Burp and choose the Send to Intruder option on.
Task 1 Intro Burp Suite a framework of web application pentesting tools is widely regarded as the de facto tool to use when performing web app testing.

0 Response to "Burp Suite Intruder Attack Types"
Post a Comment